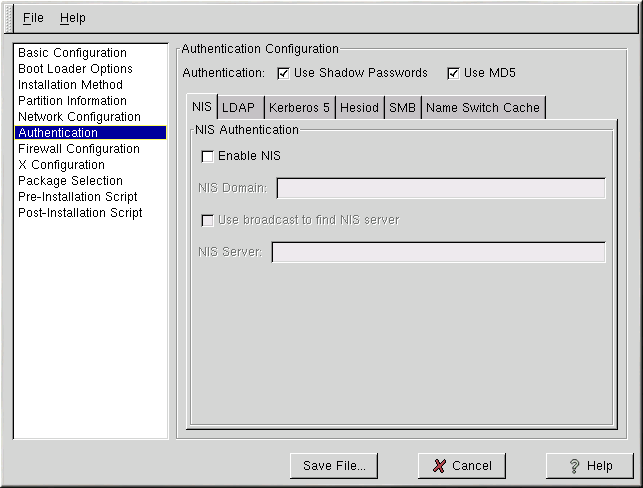
Authentication
In the Authentication section, select whether to use shadow passwords and md5 encryption for user passwords. These options are highly recommended and chosen by default.
The Authentication Configuration options allows you to configure the following methods of authentication:
NIS
LDAP
Kerberos 5
Hesiod
SMB
Name Switch Cache
They are not enabled by default. To enable one or more of these methods, click the appropriate tab, click the checkbutton next to Enable, and enter the appropriate information for the authentication method.